Recently I was tasked with setting up a remote user so that they can access a machine via VPN and then RDP-in. The performance of the Sonicwall SSL VPN has been atrocious over the past few months. The speeds over VPN has been a tenth of the available bandwidth & that can be an issue over relatively slower bandwidths. I have been doing a little research and figured that if I setup OpenSSH server on the windows box then I can setup a SSH tunnel and then RDP over this tunnel. This would be fairly secure in my opinion & would get rid of the atrocious performance by Sonicwall.
While following the suggested steps to get OpenSSH up & running I ran into multiple issues which were specific to running it on windows. I dug into a lot of different sources on the interwebs and was finally able to get this set up. Here's how I did this:
NOTES:
While following the suggested steps to get OpenSSH up & running I ran into multiple issues which were specific to running it on windows. I dug into a lot of different sources on the interwebs and was finally able to get this set up. Here's how I did this:
- Download openssh for windows from github
- Unzip the files to c:\Program Files\OpenSSH
- Also, if not present, create a new folder called log within this folder
- As the Administrator, install SSHD and ssh-agent services:
powershell.exe -ExecutionPolicy Bypass -File install-sshd.ps1 - As the Administrator, generate server keys and restrict an access to them, by running the following commands from the C:\Program Files\OpenSSH:
.\ssh-keygen.exe -A
powershell.exe -ExecutionPolicy Bypass -File .\FixHostFilePermissions.ps1 - Open a port for the SSH server on Windows Firewall.
- Configure the SSHD & SSH Agent Services to start Automatically when windows boots up. (Services > SSHD > Properties > Set start to Automatically & start the service). Make sure that you set the service to restart the service in case of failure.
- Generate a new public/private key pair using puttygen. You can get puttygen from here.
- After you generate the key, enter the user that will be used to connect to the machine, ex. ojas under "Key comment". The defaults for key type should be good (RSA/2048bit).
- Copy the key generated in that box and save it in a file, lets call it pubkey.txt. We'll use it later.
- Save both your private & public keys & keep your private key somewhere safe.
- On the Server, create a new folder called ".ssh" under c:\Program Files\OpenSSH\ . In this folder create a new file called authorized_keys. Make sure that the permissions on authorized_keys file is as follows:
- Administrators: Full Control
- SYSTEM: Full Control
- sshd: Read
- Copy the key from pubkey.txt file above to authorized_keys file & make sure that the entire string is in one line! You can add more keys to this file, but make sure that there is only one key per line.
- Now, we need to configure openssh to use this public key to authenticate instead of password based authentication. To acomplish this, open the sshd_config file, uncomment the following lines and make them look like so:
- RSAAuthentication yes
- PubkeyAuthentication yes
- PasswordAuthentication no
- PidFile \logs\sshd.pid
- Restart the service after making changes to the config file.
Connecting from Windows client:
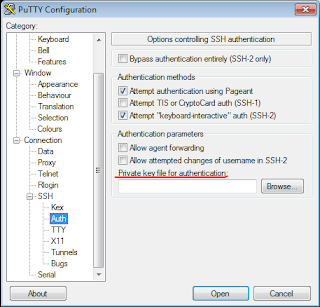
- From a client, open putty and try to connect to the openssh server that we configured above. To use public key authentication, expand SSH option in the left menu & select Auth. On the right side, click on browse & select your private key for authentication. Once you click on open, you'll be asked for a username & then for a passphrase that you used to protect your private key with.
- Once you enter the correct passphrase, you should be logged in to the server's command prompt.
- Now that we have verified that SSH is working, lets create a reverse tunnel that will forward the RDP port from windows 2016 server to your local machine over SSH.
- To do that, we'll open putty again & as in the previous step, select private key for authentication. Now, to create a tunnel, select Tunnels from the menu on the left & enter values in Source Port & Destination and don't forget to click Add.(see screenshot below)
- It is very important to understand what this is doing:
- Destination is the RDP IP/port combination as viewed from the machine you are SSH-ing to. Port 3389(RDP) is open on the windows 2016 machine, & this config defines that we will be forwarding that port over ssh to the Source port on local machine.
- Source Port is the port that will be opened on the client. If you had the settings as the screenshot above, putty will open a local port 1337 which will be forwarded through this SSH tunnel to port 3389 on the remote machine.
- You can use any Source port as long as it doesn't conflict with what you are running on the client machine
- Once you connect via putty you can RDP to your server by connecting to localhost:1337. 1337 is the same port that we set in Source above.
Connecting from OSX or Linux Client:
Here’s what you need to do from your macbook:
- Open
terminal & type the following command: ssh -L
1337:127.0.0.1:3389 11.2.1.1 -p 22 -l “domain\user” -i /
- This is essentially ssh-ing to your machine on port 22 & forwarding port 3389(RDP) to a local port 1337. Feel free to
change 1337 to whatever you’d like.
- After you press enter, you’ll be asked for passphrase
for the key, type that and press enter.
- Once the connection is established, you’ll see command
prompt. Minimize this window. As long as you have this window open, the
SSH tunnel will remain open.
- Open your remote desktop client & connect to localhost:1337.
- Login as your user & enjoy RDP access
If you run into issues with the SSH connection, edit the sshd_config file and change LogLevel to DEBUG3 & tail the sshd.log file under log folder.